2025 Cross-Chain Bridge Security Audit Guide
2025 Cross-Chain Bridge Security Audit Guide
Recent data from Chainalysis indicates that a staggering 73% of global cross-chain bridges are vulnerable to security breaches. As the cryptocurrency ecosystem evolves, understanding how to secure these vital infrastructure components has never been more important. In this article, we will explore the significance of Bitcoin on cross-chain interoperability, and how improving security protocols can protect your investments.
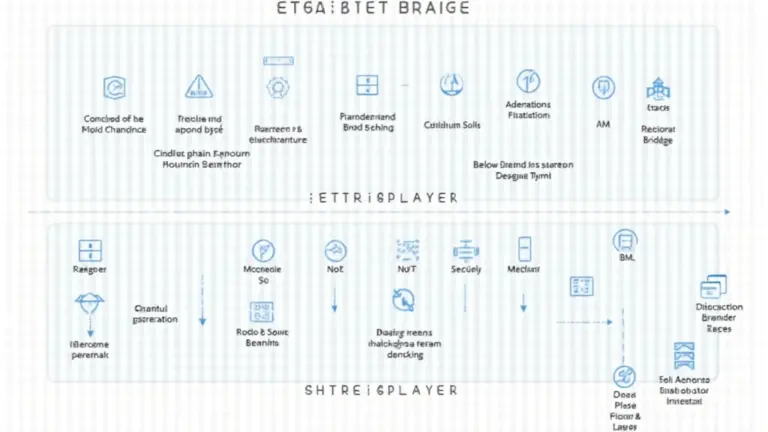
What is Cross-Chain Interoperability?
Imagine cross-chain interoperability like currency exchange booths you find in airports. Just as those booths help you convert one currency to another, cross-chain bridges facilitate transfers between different blockchain networks. This mechanism is crucial for the seamless exchange of assets, especially with the rise of decentralized finance (DeFi).
Why are Cross-Chain Bridges Vulnerable?
According to CoinGecko’s 2025 data, most vulnerabilities stem from under-tested smart contracts. Think of a smart contract like a recipe—if even a single ingredient is measured incorrectly, the outcome can be disastrous. If you’re relying on a poorly audited smart contract to execute a transaction, you’re setting yourself up for risk.
Strategies for Ensuring Bridge Security
Implementing robust security measures is like putting locks on your doors. You wouldn’t leave your house unprotected, so why leave your crypto assets vulnerable? Regular audits, real-time monitoring, and utilizing oracle services can significantly reduce the chances of a breach.
Future Trends in Cross-Chain Technology
As we look towards 2025, expect innovations such as zero-knowledge proofs to enhance privacy and security. Think of zero-knowledge proofs as a way to verify something without revealing the underlying information—like showing a ticket without revealing your destination. This new technology could vastly improve the reliability of cross-chain transactions.
In conclusion, as Bitcoin on cross-chain technology progresses, securing these bridges must remain a priority for all users. Download our comprehensive toolkit on cross-chain security and stay informed about the latest protective measures.