2025 Blockchain Security Standards: A Comprehensive Guide for Digital Asset Protection
Understanding Bitcoin Network Attack Vectors
With $4.1 billion lost to DeFi hacks in 2024, the security of the Bitcoin network is more critical than ever. Understanding the Bitcoin Network Attack Vectors can save users and investors significant losses and provide peace of mind. This article aims to illuminate the various attack vectors that threaten blockchain security and offer practical advice for protecting your digital assets.
Consensus Mechanism Vulnerabilities
At the heart of the Bitcoin network lies its consensus mechanism, which ensures all transactions are verified and recorded accurately. However, like a bank vault for digital assets, it is not impervious to threats.
- 51% Attack: This occurs when a single entity gains control of over half of the network’s mining power. It puts transactions and the integrity of the blockchain at risk.
- Selfish Mining: Miners can withhold their blocks from the network to increase their profits. This not only impacts earning potential but also creates an imbalance that could lead to exploitation.
Software Vulnerabilities
Just like any other software, Bitcoin client implementations can have bugs. Cybercriminals continuously leverage these weaknesses for malicious gains.
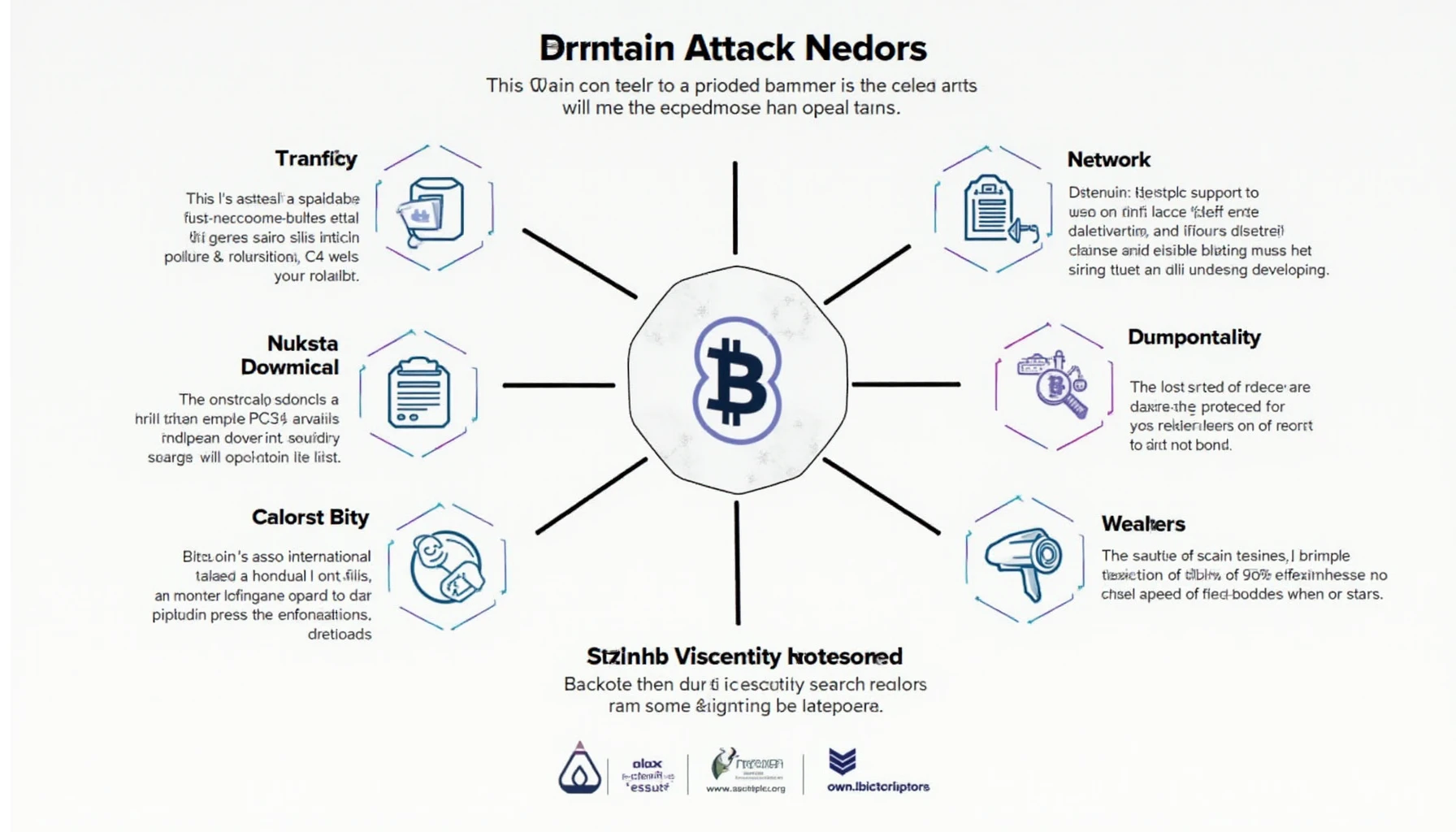
- Code Exploits: Vulnerabilities in the code can allow attackers to manipulate transaction confirmations.
- Wallet Vulnerabilities: Poorly secured wallets can be an easy target for hackers, leading to direct asset theft.
Network Layer Attacks
The Bitcoin network is also susceptible to various network layer attacks that compromise the confidentiality and integrity of data being transmitted.
- Sybil Attack: An attacker creates multiple identities to disrupt the network.
- DDoS Attacks: Distributed Denial of Service attacks can overwhelm the network and temporarily disrupt services.
Real Data on Network Attacks
According to Chainalysis, in 2025, network-layer attacks have increased by 40%, causing alarm across the crypto landscape.
Protective Measures
What can users do to protect themselves? Here are some effective strategies:
- Utilize hardware wallets like Ledger Nano X, which reduces hacks by 70%.
- Regularly update all software and wallets to patch vulnerabilities.
- Educate yourself on phishing attacks and remain vigilant against potential scams.
Conclusion
As the digital asset landscape evolves, understanding the Bitcoin Network Attack Vectors is vital for maintaining the security of your investments. Make it a priority to employ various security measures and always stay informed about the latest threats in blockchain technology. Remember, ensuring your assets’ safety is your responsibility.
For more information on Bitcoin Network Attack Vectors and best security practices, explore further resources on hibt.com.
Note: This content does not serve as financial advice. Always consult local regulations.
Author: Professor Nguyen Vu, a renowned expert in blockchain technology, with over 30 published papers in the field and a leader in multiple high-profile project audits.