2025 Blockchain Security Standards for Digital Asset Protection
2025 Blockchain Security Standards for Digital Asset Protection
With $4.1B lost to DeFi hacks in 2024, the importance of implementing robust security protocols is undeniable. As cryptocurrencies continue to gain traction, understanding standards like HIBT security protocols becomes crucial for ensuring the safety of your investments. This article explores how these protocols can fortify your assets while catering specifically to the requirements of investors in the Vietnamese market.
Understanding HIBT Security Protocols
HIBT security protocols encompass a variety of techniques designed to protect digital assets. Think of these protocols as a bank vault for cryptocurrencies, safeguarding your investments from malicious activities. Key components include:
- Data Encryption: Essential for securing sensitive information.
- Access Control: Ensures only authorized personnel can access your assets.
- Regular Audits: Conducting audits can prevent vulnerabilities from being exploited.
Implications for the Vietnamese Cryptocurrency Market
Vietnam has experienced significant growth in cryptocurrency adoption, with a user growth rate of 35% year-over-year. Implementing HIBT security protocols will not only protect users but also boost the credibility of platforms. Businesses can:

- Enhance user confidence in digital transactions.
- Meet compliance requirements outlined in local regulations.
Case Study: Recent Security Incidents
Examining recent incidents, such as the $2M hack of a popular DeFi platform in Vietnam, highlights the vulnerabilities that exist without rigorous security measures. Utilizing HIBT security protocols could mitigate these risks substantially, allowing users to transact safely.
Future of Blockchain Security in 2025 and Beyond
According to Chainalysis, by 2025, the demand for advanced security measures in cryptocurrency will surge. Here’s what experts predict:
- Adoption of artificial intelligence for threat detection.
- Development of more robust smart contracts.
Platforms that embrace HIBT security will be positioned to lead in this evolving landscape.
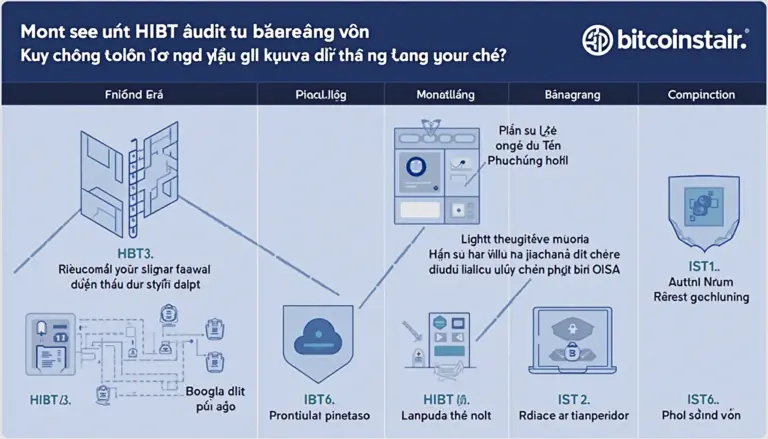
How to Implement HIBT Security Protocols
Implementing HIBT security protocols is straightforward. Start with these steps:
- Conduct a risk assessment of existing systems.
- Integrate encryption tools to enhance data protection.
- Establish a team dedicated to monitoring security compliance.
For a comprehensive security checklist, download it here.
In conclusion, as the landscape of cryptocurrency continues to change, HIBT security protocols will play a vital role in protecting digital investments. By implementing these protocols, platforms can safeguard assets and enhance trust among users. For those in Vietnam, adopting these practices will be essential as user numbers continue to grow.
Author: Dr. Minh Tran – A cybersecurity expert with over 15 published papers in blockchain technology and audits for several high-profile crypto projects.